IMPLEMENTASI COSINE SIMILARITY DALAM ANALISIS INVESTIGASI CYBERBULLYING PADA TWITTER DENGAN FRAMEWORK NIST
DOI:
https://doi.org/10.14421/csecurity.2022.5.1.3397Abstract
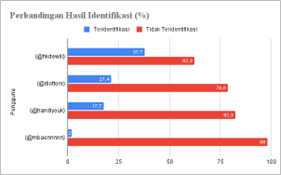
Pengguna Twitter di Indonesia pada tahun 2021 tercatat mencapai 63,6% dari jumlah populasi dan menempati urutan ke-5 sosial media yang sering diakses oleh masyarakat Indonesia. Semakin tingginya tingkat pengguna Twitter memberi peluang bagi penggunanya untuk melakukan cybercrime seperti cyberbullying. Korban cyberbullying rentan terkena depresi dibandingkan dengan korban tindakan kekerasan verbal lainnya. Melihat dampak yang ditimbulkan maka diperlukan langkah-langkah untuk mengatasi cyberbullying dengan investigasi forensik untuk membuktikan dan menemukan bukti digital yang membantu menyelesaikan kasus cyberbullying yang marak terjadi di media sosial seperti pada Twitter, sehingga dapat diajukan sebagai bukti kuat, konkrit, serta dapat diproses di pengadilan. Tujuan dari penelitian ini untuk menemukan bukti digital dan mengidentifikasi tindakan cyberbullying pada fitur pesan grup Twitter dengan alur kerja NIST (National Institute of Standards and Technology). Penelitian ini berhasil mendapatkan bukti digital berupa teks percakapan pada smartphone korban yang diekstrak dengan tools MOBILEdit Forensic Express dan dianalisis dengan text processing, pembobotan term/kata, dan menerapkan formula cosine similarity untuk mengidentifikasi cyberbullying. Hasil penelitian menujukkan alur kerja NIST berhasil mengangkat barang bukti hingga pelaporan barang bukti. Metode cosine similarity berhasil mengidentifikasi kalimat yang terindikasi bullying dengan nilai yang berbeda, pelaku dengan nilai tertinggi mencapai 0,377, sedangkan pelaku dengan nilai terendah menyentuh angka 0,02 berdasarkan dengan percakapan terhadap query (kata kunci) bullying.
Kata kunci: digital forensik, cyberbullying, cosine similarity, nist, twitter
------
Twitter users in Indonesia in 2021 are recorded at 63.6% of the total population and ranks 5th on social media that are often accessed by Indonesian people. The higher level of Twitter users provides opportunities for users to commit cybercrime such as cyberbullying. Victims of cyberbullying are more prone to depression than other victims of verbal abuse. Seeing the impact, it is necessary to take steps to overcome cyberbullying with forensic investigations to prove and find digital evidence that helps resolve cyberbullying cases that are rife on social media such as Twitter, so that it can be submitted as strong, concrete evidence, and can be processed in court. The purpose of this study was to find digital evidence and identify acts of cyberbullying on the Twitter direct message group with the NIST (National Institute of Standards and Technology) methodology. This study succeeded in obtaining digital evidence in the form of text conversations on the victim's smartphone which was extracted with the MOBILEdit Forensic Express tool and analyzed by text processing, weighting terms/words, and applying the cosine similarity formula to identify cyberbullying. The results of the study show that the NIST has succeeded in raising evidence to reporting evidence. The cosine similarity method succeeded in identifying sentences that indicated bullying with different values, the perpetrator with the highest score reached 0.377, while the perpetrator with the lowest score touched 0.02 based on conversations about the bullying query (keyword).
Keywords: digital forensic, cyberbullying, cosine similarity, nist, twitter
References
Downloads
Published
Issue
Section
License
Copyright (c) 2022 Eno Hakimah Kusuma Dewi, Aries Suharso, Chaerur Rozikin

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Attribution-ShareAlike 4.0 International (CC BY-SA 4.0)
You are free to:
- Share — copy and redistribute the material in any medium or format
- Adapt — remix, transform, and build upon the material for any purpose, even commercially.
Under the following terms:
- Attribution — You must give appropriate credit, provide a link to the license, and indicate if changes were made. You may do so in any reasonable manner, but not in any way that suggests the licensor endorses you or your use.
- ShareAlike — If you remix, transform, or build upon the material, you must distribute your contributions under the same license as the original.
- No additional restrictions — You may not apply legal terms or technological measures that legally restrict others from doing anything the license permits.



