Analisis Forensik Digital Aplikasi Signal Desktop Pada Windows 11 Menggunakan Metodologi Forensik Digital Berbasis ISO/IEC 27037:2012 Dan ISO/IEC 27042:2015
DOI:
https://doi.org/10.14421/csecurity.2025.8.2.5387Abstract
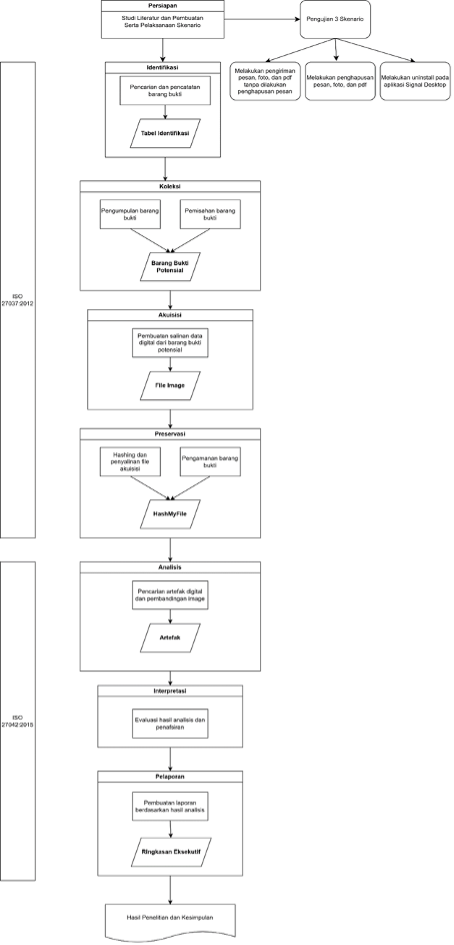
Aplikasi Signal merupakan aplikasi pesan singkat yang dikenal dengan tingkat keamanan dan privasi yang tinggi. Meskipun demikian, keunggulan aplikasi ini sering dimanfaatkan oleh pelaku kejahatan untuk menyembunyikan atau menghilangkan barang bukti digital terutama pada platform Windows. Penelitian ini akan melakukan analisis forensik digital aplikasi Signal Desktop untuk menemukan bukti digital pada platform Windows 11 menggunakan metode ISO/IEC 27037:2012 dan ISO/IEC 27042:2015. FTK Imager dan Autopsy digunakan sebagai alat bantu forensik. Analisis forensik akan dilakukan dengan tiga skenario yang telah ditetapkan. Hasil penelitian menunjukkan bahwa artefak digital seperti teks, video, gambar dan file pdf dapat ditemukan dengan metode forensik yang sesuai, namun penghapusan data dan proses pencopotan aplikasi berdampak pada hasil artefak digital yang ditemukan. Penelitian ini juga membuktikan bahwa ISO/IEC 27037:2012 dan ISO/IEC 27042:2015 dapat digunakan untuk mengumpulkan, menganalisis, dan menginterpretasikan bukti digital secara sistematis.
Kata kunci: Forensik Digital, Signal Desktop, Windows 11, ISO/IEC 27037:2012, ISO/IEC 27042:2015, FTK Imager, Autopsy
--------------------------------------------------------------------------------------------------
Digital Forensic Analysis Of Desktop Signal Applications On Windows 11 Using Digital Forensic Methodology Based On ISO/IEC 27037:2012 And ISO/IEC 27042:2015
The Signal application is an instant messaging platform well-known for its high level of security and privacy through the use of end-to-end encryption. However, these advantages are often exploited by criminals to conceal or erase digital evidence, especially on the Windows platform. Previous studies have demonstrated the effectiveness of forensic methods on Signal Messenger mobile devices using various tools and frameworks, but research on Signal Desktop artifacts in the latest operating systems remains limited. This study explores digital artifacts of Signal Desktop on Windows 11 to identify potential digital evidence that can be recovered. The methodology applies ISO/IEC 27037:2012 for the identification, collection, acquisition, and preservation of evidence, and ISO/IEC 27042:2015 for the analysis, interpretation, and reporting stages. The forensic tools employed are FTK Imager for data acquisition and Autopsy for artifact analysis. The experiment was conducted using three scenarios: normal usage without deletion, deletion of messages and files, and application uninstallation. The results show that digital artifacts such as text messages, images, videos, and PDF files can be retrieved in normal usage. In the deletion scenario, images, videos, and PDF files were recoverable as deleted files, whereas text messages were unrecoverable. In the uninstallation scenario, most artifacts were no longer accessible. These findings confirm that ISO/IEC 27037:2012 and ISO/IEC 27042:2015 provide a systematic and reliable framework for acquiring, preserving, and analyzing digital evidence in the context of Signal Desktop..
Keywords: Digital Forensics, Signal Desktop, Windows 11, ISO/IEC 27037:2012, ISO/IEC 27042:2015, FTK Imager, Autopsy
References
Downloads
Published
Issue
Section
License
Copyright (c) 2025 Ahmad Anwary Adzirudin

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Attribution-ShareAlike 4.0 International (CC BY-SA 4.0)
You are free to:
- Share — copy and redistribute the material in any medium or format
- Adapt — remix, transform, and build upon the material for any purpose, even commercially.
Under the following terms:
- Attribution — You must give appropriate credit, provide a link to the license, and indicate if changes were made. You may do so in any reasonable manner, but not in any way that suggests the licensor endorses you or your use.
- ShareAlike — If you remix, transform, or build upon the material, you must distribute your contributions under the same license as the original.
- No additional restrictions — You may not apply legal terms or technological measures that legally restrict others from doing anything the license permits.



